最近同事在办公网登录 aws 控制台(ap-southeast-1.console.aws.amazon.com),浏览器提示证书异常,怀疑IT做了劫持(我们做过一些网站的劫持,劫持到sniproxy,进行透明代理):
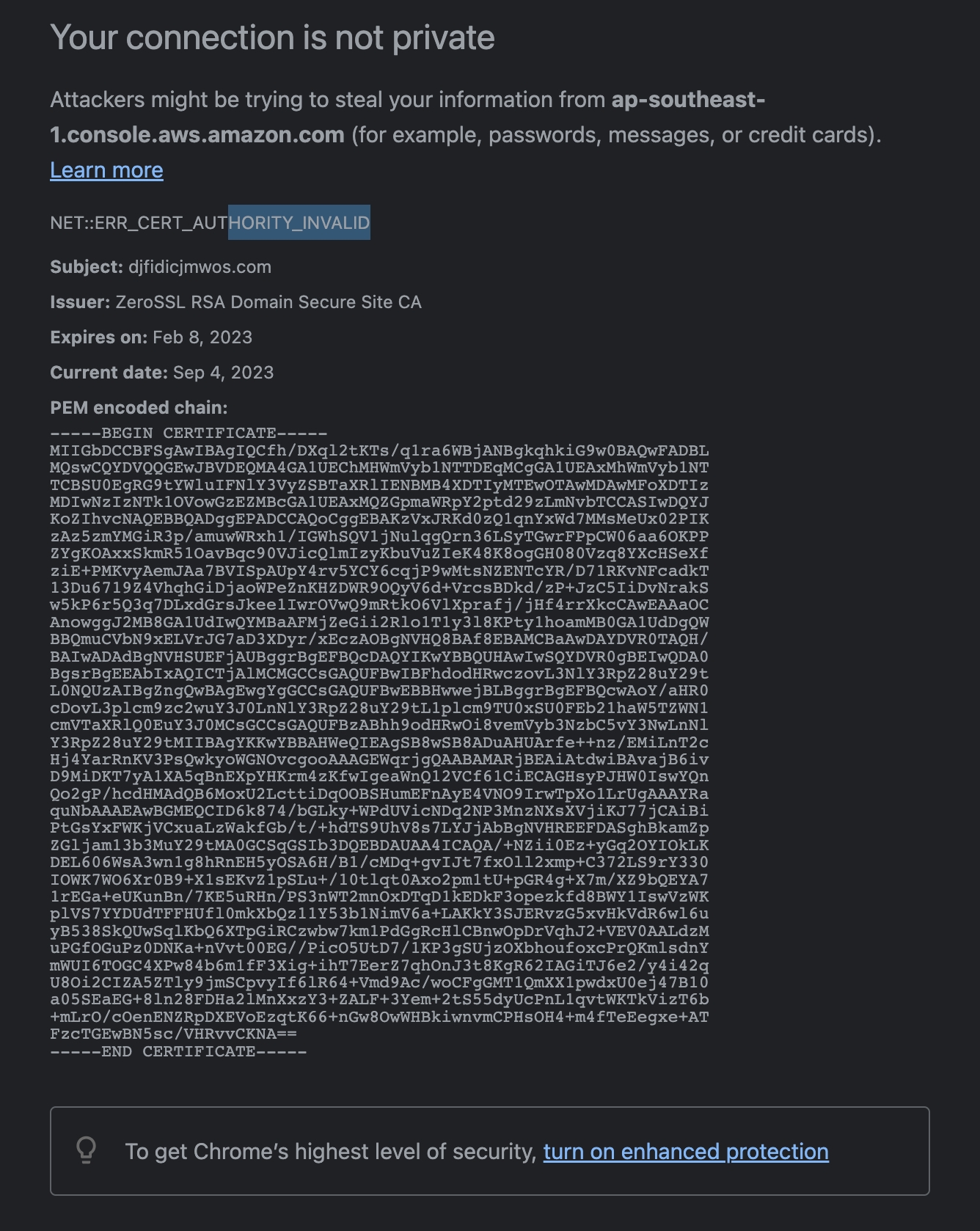
里面的域名是 djfidicjmwos.com, 搜索这个域名,有一个类似的帖子:部分网站登录时不时提示“你的连接不是专用连接”,然后进不去后,等会又可以进。
查看办公网的localdns,上游是深圳电信返回:
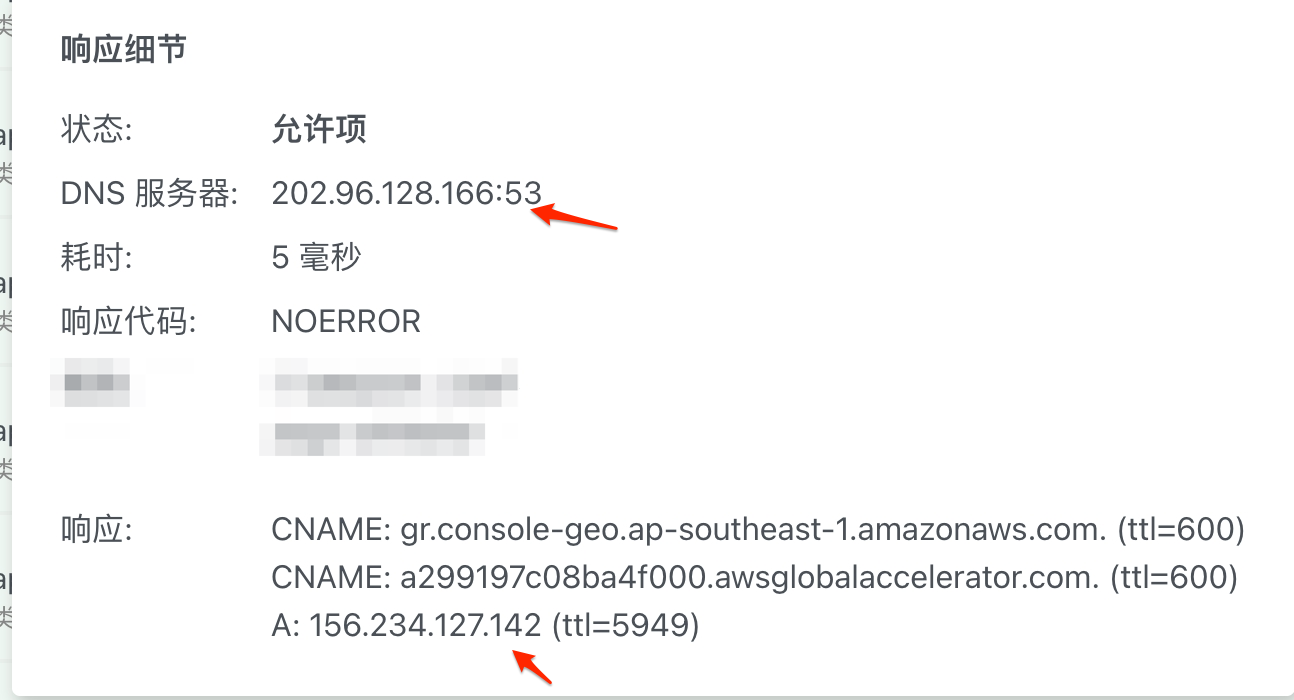
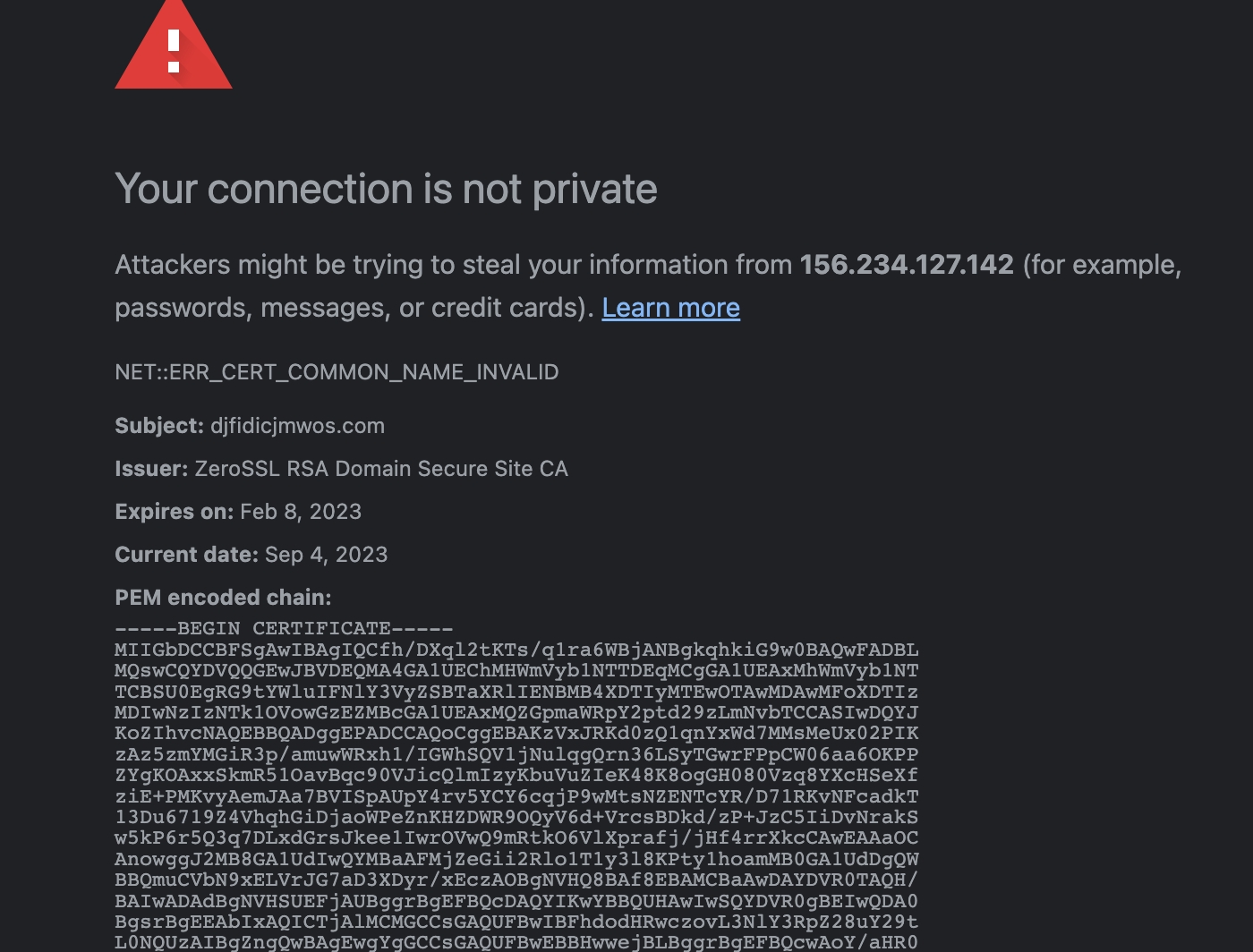
可疑IP:156.234.127.142
直接访问这个IP 的https端口,返回证书和劫持一致:
序列号 9F87F0D7AA5DAD293B3FAB5ADAE9606
根证书 否
算法 SHA384WithRSA
证书类型 DV
证书品牌 Comodo
私钥长度 2048 Bits
SHA1指纹 6BB71F0A72CD9DC0E51117373957DB4036B475F5
SHA256指纹 F3B1564D750EFE874AC166D427BC5ACF7E4554BEFCF3988B7F0EE069905A0B02
公钥PIN-SHA256 aSE+RSj9ELhDFz+sK8mVtlJQ0gUX2j0sTRHQa69sjco=
按这个IP查询ti.360.net ,看起来和博彩相关:
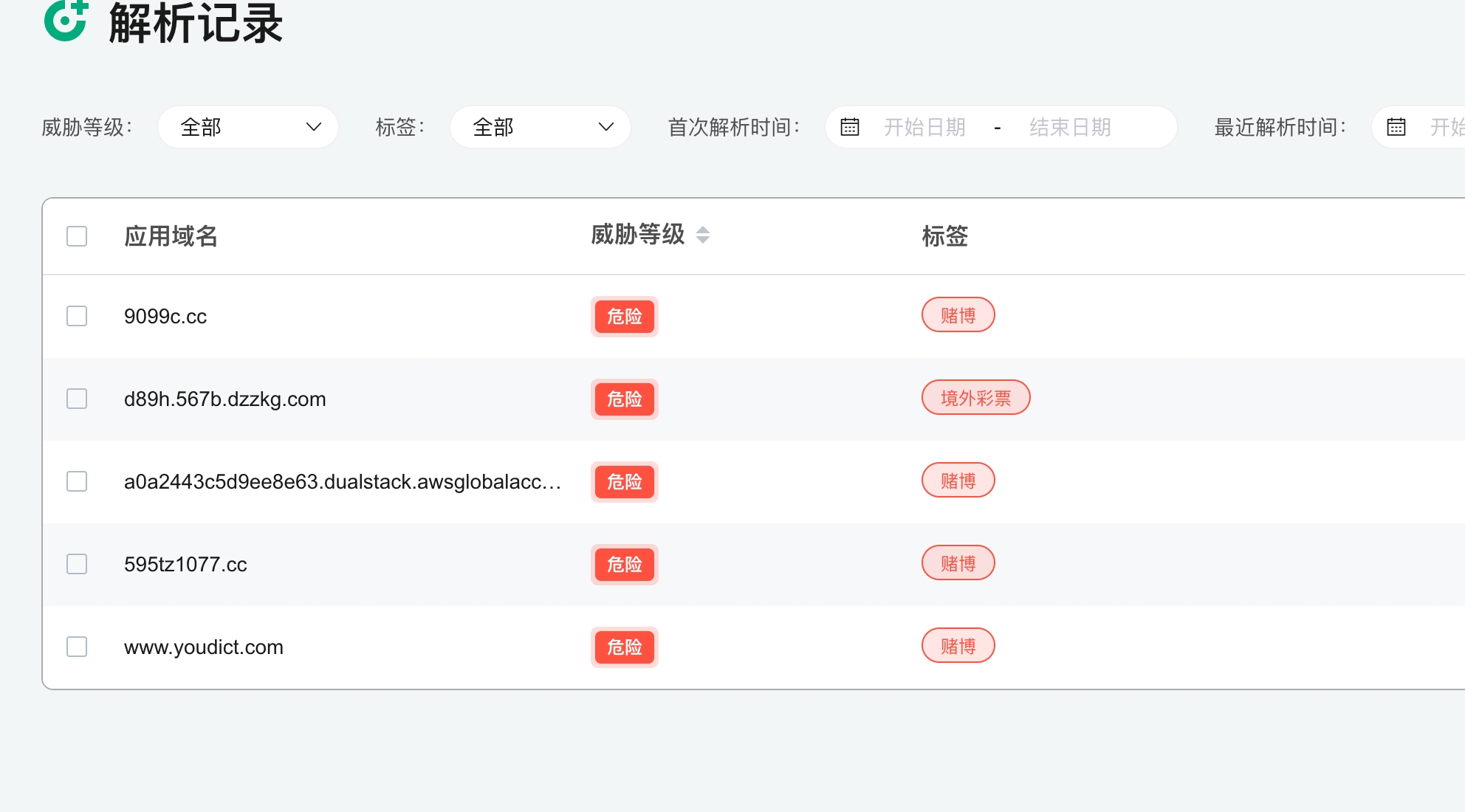
直接对202.96.128.166 发起请求,会间歇性返回这个IP,可能只是集群中某台服务器异常 , 这条记录的TTL特别长。
dig @202.96.128.166 ap-southeast-1.console.aws.amazon.com
; <<>> DiG 9.10.6 <<>> @202.96.128.166 ap-southeast-1.console.aws.amazon.com
; (1 server found)
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 42939
;; flags: qr rd ra; QUERY: 1, ANSWER: 3, AUTHORITY: 4, ADDITIONAL: 8
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 4096
;; QUESTION SECTION:
;ap-southeast-1.console.aws.amazon.com. IN A
;; ANSWER SECTION:
ap-southeast-1.console.aws.amazon.com. 600 IN CNAME gr.console-geo.ap-southeast-1.amazonaws.com.
gr.console-geo.ap-southeast-1.amazonaws.com. 600 IN CNAME a299197c08ba4f000.awsglobalaccelerator.com.
a299197c08ba4f000.awsglobalaccelerator.com. 2206 IN A 156.234.127.142
;; AUTHORITY SECTION:
awsglobalaccelerator.com. 46274 IN NS ns-1484.awsdns-57.org.
awsglobalaccelerator.com. 46274 IN NS ns-409.awsdns-51.com.
awsglobalaccelerator.com. 46274 IN NS ns-609.awsdns-12.net.
awsglobalaccelerator.com. 46274 IN NS ns-1949.awsdns-51.co.uk.
;; ADDITIONAL SECTION:
ns-1949.awsdns-51.co.uk. 2130 IN A 205.251.199.157
ns-409.awsdns-51.com. 42961 IN A 205.251.193.153
ns-609.awsdns-12.net. 67319 IN A 205.251.194.97
ns-1484.awsdns-57.org. 85695 IN AAAA 2600:9000:5305:cc00::1
ns-1949.awsdns-51.co.uk. 2130 IN AAAA 2600:9000:5307:9d00::1
ns-409.awsdns-51.com. 42961 IN AAAA 2600:9000:5301:9900::1
ns-609.awsdns-12.net. 47034 IN AAAA 2600:9000:5302:6100::1
;; Query time: 1113 msec
;; SERVER: 202.96.128.166#53(202.96.128.166)
;; WHEN: Mon Sep 04 17:09:16 CST 2023
;; MSG SIZE rcvd: 486
请求114.114.114.114 ,返回的是:156.234.127.138,一个C段,直接返回https 443端口,返回一样的证书。阿里的223.5.5.5,还有一个C段IP:156.234.127.27。
DNSPod 的119.29.29.29 多次测试,没发现异常。 1.1.1.1 和 8.8.8.8多次测试,也无异常。
正常响应是3.3.15.1 和3.3.14.1:
ap-southeast-1.console.aws.amazon.com. 126 IN CNAME gr.console-geo.ap-southeast-1.amazonaws.com.
gr.console-geo.ap-southeast-1.amazonaws.com. 126 IN CNAME a299197c08ba4f000.awsglobalaccelerator.com.
a299197c08ba4f000.awsglobalaccelerator.com. 186 IN A 3.3.15.1
a299197c08ba4f000.awsglobalaccelerator.com. 186 IN A 3.3.14.1
有人说可能aws 的系统出问题了,我觉得可能性不大。猜测几个可能的原因:
- 电信某一组服务器被入侵?不太可能,114 也出现了类似情况;
- 跨境的中间链路上有dns 抢答,注入了恶意地址?好像可能性也不大;
- 权威服务器的某个IP在某个域内BGP Leak 了? 牵引了部分权威服务器的流量,然后进行抢答;
- DNS 缓存投毒(DNS cache poisoning);
个人觉得可能性比较大的是 dns 缓存投毒了 ,有人猜测了dns查询事务id,进行了抢答。
由于此劫持时间超长,影响范围超广,让我怀疑不是黑客所谓,更倾向于原因 2,是的,就是你想的那个。@20240315
什么是DNS 缓存投毒,可参考:cloudflare: What is DNS cache poisoning? | DNS spoofing ,这个幻灯片讲解的比较详细 Anatomy of a DNS Cache Poisoning Attack。
规避方法,使用DNSSEC,或者不使用固定的源地址,随机源地址+随机事务ID,让攻击者更难猜测:
- UDP Source Port Randomization (UDP SPR): What this does is setting the UDP
source port randomly, so an attacker would have to guess both the transaction ID
and the source port in a short time window - which is usually not feasible (since they
would need to make 232 combinations).
- DNS Security Extensions (DNSSEC): It is a protocol designed to create a unique
cryptographic signature and store it alongside other DNS records. Thus, DNSSEC
provides DNS with an additional methods of verification by digitally signing the DNS
information. This is done on all levels of the DNS Resolution process.
从这篇文章看:
该变种攻击漏洞影响 Linux 内核以及流行的 DNS 软件,包括在 Linux 上运行的 BIND、Unbound 和 dnsmasq,但在其他操作系统如 FreeBSD 或 Windows 上运行的这些DNS软件则不会。
难道是因为DNSPod 是自研,所以没受影响?
最后: 深圳电信有3组内部DNS服务器,另外2组没受影响,注释掉有问题的这个地址临时规避了。
IOCs:
- 156.234.127.142
- 156.234.127.138
- 156.234.127.27
其他参考链接: